Here are 13 ways hackers try to take over your iPhone
 Hackers work hard to hide their activities and hope you don’t notice when they steal your identity and your data from your iPhone.
Hackers work hard to hide their activities and hope you don’t notice when they steal your identity and your data from your iPhone.
Apple works hard to maintain its reputation for security and privacy. It reduces the risk of iPhones being hacked by offering security bounties to software developers and ethical hackers to identify compromising iPhone hacks. Apple then resolves the bugs in subsequent versions of iOS.
To continuously protect your security and privacy, you need to be vigilant. For each of the ways your iPhone can be hacked, here’s how you can:
- Minimize the risk of these hacks.
- Recognize that your iPhone has been hacked.
- Recover from successful hacks.
Here are 13 ways hackers try to take over your iPhone:
Email from Apple
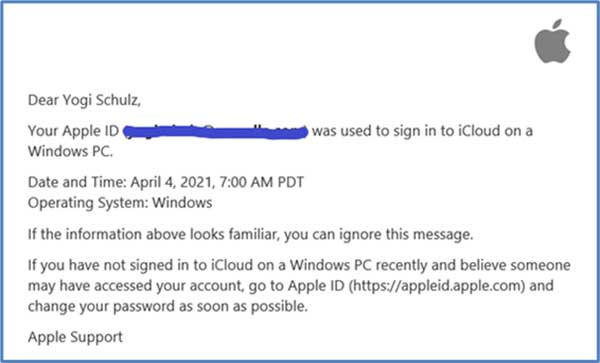
When an email like this one pops up in your inbox, it either confirms that Apple’s high-profile attention to security and privacy works or that you’ve been hacked.
If this email was triggered by you logging into iCloud from your new Windows PC, be happy Apple is monitoring access. If you can’t remember logging into iCloud from a new device, there’s someone who shouldn’t know your Apple ID and password.
Change your password immediately if you believe there is even the slightest possibility that your Apple ID has been compromised. Then follow the steps at Apple support to confirm your personal information and secure your Apple ID.
Unsecured Wi-Fi
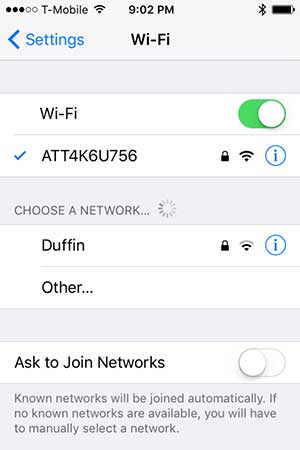
Wi-Fi in public places, such as cafés or stores, is often unsecured for patrons’ convenience. However, unsecured Wi-Fi allows malicious hackers to easily intercept your data stream while connected. Such interception attempts are known as man-in-the-middle attacks. In this attack, a hacker intercepts the data stream without anyone receiving any indication of interception. The risk of such an attack is the same for nationally recognized brands operating with greater security awareness as it is for local businesses.
The lack of the small black padlock symbol indicates an unsecured Wi-Fi network on an iPhone, as shown on the left.
Some businesses create the illusion of security consciousness by using a secure Wi-Fi network and then posting the password on a sign on the wall that all customers can see. Unfortunately, this configuration is no better than providing an unsecured Wi-Fi connection. The password, which serves as a private key for encryption, is now a public key available to hackers to decrypt all data streams.
A simple alternative that eliminates this risk is to use your cellular connection and pay for data when you need to connect where you do not have private credentials for a secure Wi-Fi network.
You can also protect yourself against these hackers using Virtual Private Network (VPN) software and its associated service. Even if a hacker intercepts your Wi-Fi data stream using a VPN, the data is highly encrypted and, therefore, useless to the hacker.
Malicious apps
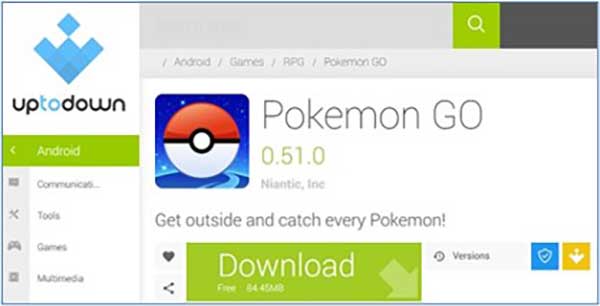
Applications add helpful features to iPhones but also increase the risk of a data breach. This risk increases significantly when you download apps from untrusted websites, as shown here. Malware that allows hackers to steal your data is almost always hidden in these malicious apps. This is true even if the apps perform the functionality you’re expecting.
A good example was the Pokémon Go craze. That phenomenon encouraged unscrupulous hackers to offer malicious apps under the guise of providing improved features, access to supposedly secret commands or improved game performance.
How to protect yourself from a data breach caused by malicious apps:
- Download apps only from the Apple App Store. Do not download apps from an email or text message link. These sources are usually malicious spam from hackers.
- Read at least one review for each app you want to download. Reviews will alert you to potentially malicious apps.
- Ignore apps that claim to improve the performance of your game or iPhone in any way. Apps can’t actually accomplish this feat.
- Limit the number of apps you install to the ones you know you will actually use.
- Report malicious iPhone apps when you come across them. Launch the App Store app. Tap Account, then tap the app in question. Scroll down and tap Write a Review to warn others of the problem.
- Delete apps you no longer use.
Occasionally, the App Store has been tricked into distributing malicious apps, as described in this article. The problem is the large number of apps submitted for certification daily overwhelms the App Store staff.
Unsecured websites
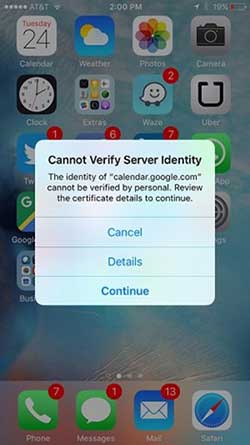
When you see this server identity dialogue box, one of your iPhone’s active tasks is contacting a website but cannot verify the authenticity of the certificate for that website.
Before casually clicking on Continue, think for a moment. Are you sure you don’t have a rogue app on your iPhone? Did you make an error entering the domain name? Do you trust the domain name displayed? Have you ever been there?
If you answered no, someone is trying to lead you to a fake website that masquerades as a popular website you visit regularly. This hack can be a typosquatting or a DNS spoofing/poisoning attack. The hacker aims to infect your iPhone with malware and breach your data.
Since google.com is a trusted domain name, the hacker has manipulated the Domain Name System (DNS) records on your iPhone or elsewhere along your DNS resolution chain.
To protect yourself and your data, click Cancel when this dialogue box appears. Generally, enter domain names carefully. If this happens more than once, it’s time for technical assistance to remove rogue apps that have infected your iPhone.
If you are technically inclined, you can check the DNS IP addresses on your network adapter settings and your gateway’s DHCP settings.
Evil twin Wi-Fi
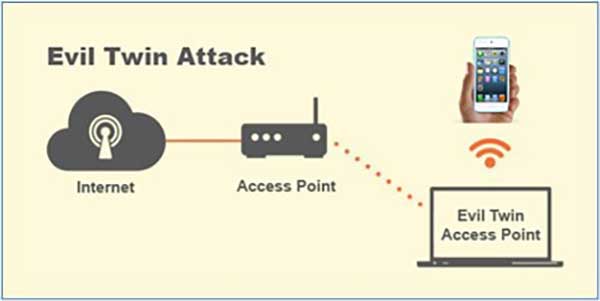
An evil twin is a fraudulent Wi-Fi access point that appears legitimate. It claims to be one of the Wi-Fi access points on the list of Wi-Fi access points your iPhone knows and will automatically connect to when it searches for a Wi-Fi connection.
The hacker’s aim is to intercept wireless communications to steal user data and passwords or send malicious content back to you. The evil twin is the wireless network equivalent of the phishing scam.
The hacker has configured the evil twin access point to pass traffic through to the legitimate Wi-Fi access point while monitoring the victim’s data stream. This pass-through approach ensures the victim is oblivious to the hacker’s presence.
To protect yourself from an evil twin hacker, check the name of the Wi-Fi access point you are connected to under Settings. If the name shown is for a Wi-Fi access point that you know is located somewhere else, such as your home, then you’ve fallen victim to this hacker. You should turn off your Wi-Fi network immediately. Then use your cellular network connection and pay for data if you must connect.
Scam emails
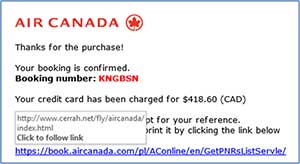
Enticing you to click on a link in an email is a common way hackers use to steal your data or install malware on your iPhone. This gambit is called a phishing attack.
Hackers send messages that use strong, assertive language to deceive us and appear to come from our bank or another trusted source, such as a merchant. However, your bank will never require you to change your password and send you a link to do so. Likewise, the government does not communicate personal tax information by email.
Glide over, but don’t click the link in a text message or an email to see exactly where the link will send you if you click on it. This is an easy way to distinguish legitimate messages from hacker messages. Just reading the text of the displayed link is not enough.
In the above example email, the hacker pretends to be Air Canada. By gliding over the prominent blue link, you reveal the actual Uniform Resource Locator (URL) to which the link refers. As the actual URL has nothing to do with Air Canada, it is a dangerous phishing message.
Delete emails from unknown senders. Some messages are intended to cause panic by claiming your credit card has been charged. Other messages ask for your information. In any case, you should not click on email links without investigation.
Juice-jacking
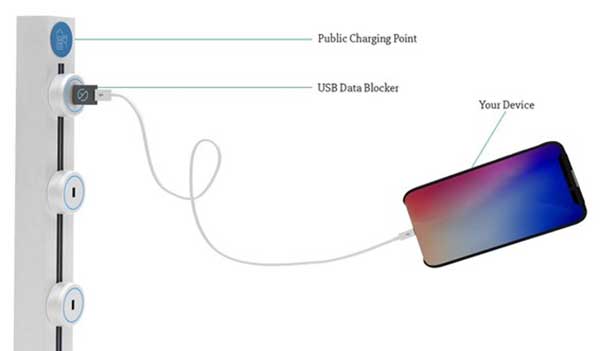
Juice-jacking occurs when hackers install a hacking device in charging stations in public places such as airports and train stations. The device installs malware on your iPhone or copies data from it as soon as you plug it in to charge it.
To eliminate this risk, a data blocker is a simple USB dongle between the USB socket and your USB charging cable. It only connects the USB power pins and blocks the data pins. This wiring prevents all data traffic in both directions.
Scam texts
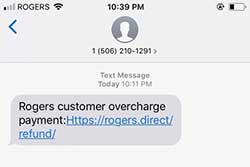 Enticing you to click on a link in a text message is a common trick hackers use to steal your data or install malware on your iPhone. This gambit is called a phishing attack.
Enticing you to click on a link in a text message is a common trick hackers use to steal your data or install malware on your iPhone. This gambit is called a phishing attack.
To fool us, hackers send texts that use phrases designed to panic us to click on a dangerous link.
In the above example email, the hacker pretends to be Rogers Communications. However, if you read the URL carefully, you will see it is not the Rogers domain name. This is a dangerous phishing message.
Delete these texts immediately. Don’t click on links in texts without investigation.
SIM swap scams
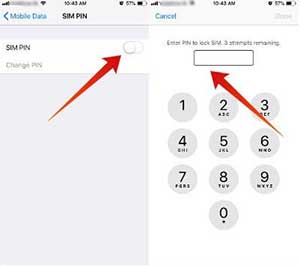
One way hackers can impersonate and steal your data is to steal your iPhone. You might think hackers can’t use your stolen iPhone because it’s locked. Also, they don’t have your face or thumbprint and don’t have your Apple ID. However, they can just take out your SIM card, insert it into their iPhone and start using it immediately without any issues.
To protect yourself from this hack, set a SIM PIN as follows:
- To find the default SIM PIN based on your carrier, enter “default sim pin” in your preferred search engine.
- If this doesn’t work, contact your carrier.
- With the 4-digit PIN in hand, go to Settings > Cellular > SIM PIN.
- Enter the default PIN and tap Done.
- The SIM PIN toggle changes to the usual green colour.
- Tap Change PIN.
- Enter your current PIN and tap Done.
- Then, enter your new PIN and tap Done.
- Next, re-enter your new PIN once again for confirmation and tap Done.
- Write down your new PIN with the rest of your user IDs and passwords.
Cellular network spoofing
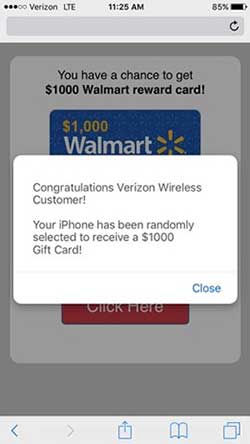
With some expensive equipment and a lot of technical know-how, hackers are beginning to learn how to spoof cellular networks to carry out man-in-the-middle attacks.
Hackers choose crowded public places, like museums or airports, for this hack. These places are attractive because there are many active iPhones, we’re focused on another activity, and we are less vigilant because we expect reasonable security.
In the screenshot on the left, I’m connected to the Verizon LTE cellular network instead of Wi-Fi.
In this example, the hacker tries to trick me into clicking on the incorrectly labelled web page link to claim my non-existent prize. If I click as suggested, I cause malware to install itself on my iPhone.
To thwart this attack, the best action is to double-tap the Home button to reveal all active apps in the Multitasking Manager. Then quickly swipe the Safari app up so it’s no longer active. You also want to place your iPhone in Airplane Mode until you reach a safer place far from the original interception point. These actions prevent the hacker from intercepting your website credentials.
To protect yourself and your data, be careful when clicking on web page links to avoid downloading malware that collects personal information. Please note that the mobile phone carrier is not involved in this attack. If you experience the same problem at the venue a second time, you should contact the management and encourage them to call the police to investigate the hacker.
Strange iPhone behaviours

Someone who has sneaked a malicious app onto your iPhone may have hacked your iPhone as well. It is possible even though it requires a lot of technical expertise. Here are some indicators that your iPhone contains such a malicious app.
Your battery loses its charge quickly, even when you’re not using your iPhone, because the malicious app consumes power while sending your data to its controller.
You see multiple, random, inexplicable screen flashes. Flashes are a common indication of a software flaw in an app or the presence of a malicious app. If the flashes persist on your Home screen after a reboot when no apps are supposed to be running, you likely have a malicious app.
The data usage on your monthly iPhone bill or under Settings, tap Cellular, is much higher than your estimate of actual use. The difference is a good indicator that you have a malicious app.
Some malicious apps are smart enough to transmit only when you’re connected to Wi-Fi. Hackers know iPhones have no built-in way to see Wi-Fi data usage like Android. You can install an iPhone app to track Wi-Fi data usage. Here’s a link to a review of data usage apps.
If your iPhone exhibits strange behaviour, you should immediately turn it off. Then seek technical help to remove the malicious app from your iPhone.
iOS vulnerabilities

Even with Apple’s considerable software testing effort, iOS vulnerabilities remain and will be discovered by unscrupulous actors. These flaws can allow hackers to infiltrate your iPhone. Some of the flaws allow hackers to steal your data. Others enable hackers to access and control your iPhone remotely.
To correct vulnerabilities and protect end-users, Apple frequently releases iOS updates. Your iPhone indicates an update can be installed by displaying a one on the Settings icon as shown on the left.
To protect yourself, install iOS updates as soon as they become available. This action is essential because, once updates are released, your risk of being hacked actually increases if you fail to install the update. This counter-intuitive situation arises because hackers now know the technical details of the corrected defects and will use that knowledge to attempt breaches of un-updated iPhones.
App software defects
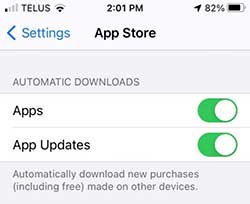
Despite the best intentions of iPhone app developers, software defects are eternal and will be discovered by end-users in due course. Sometimes these defects can let hackers steal your identity and your data.
IPhone app developers publish app updates to correct software defects and protect end-users. By default, your iPhone automatically downloads and installs available app updates from the App Store based on the settings shown on the left.
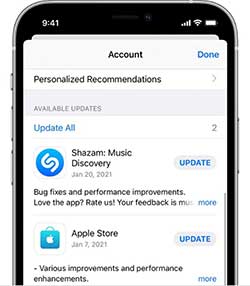 If you want to carefully control which apps to update and when, change the Setting from automatic. The App Store app will display all available app updates for you to select, as shown on the left.
If you want to carefully control which apps to update and when, change the Setting from automatic. The App Store app will display all available app updates for you to select, as shown on the left.
To protect yourself, install app updates as soon as they become available.
If you suspect you have installed a malicious app by mistake, delete it immediately. If you later find out you were wrong, it’s easy to reinstall.
Yogi Schulz has over 40 years of information technology experience in various industries. His specialties include IT strategy, web strategy and project management.
For interview requests, click here.
The opinions expressed by our columnists and contributors are theirs alone and do not inherently or expressly reflect the views of our publication.
© Troy Media
Troy Media is an editorial content provider to media outlets and its own hosted community news outlets across Canada.
